-
 13 min. read
13 min. read
-
 WebFX Team
WebFX Team Digital Marketing Agency
Digital Marketing Agency
- The WebFX team is made up of more than 450 subject matter experts in digital marketing, SEO, web design and web development, social media, and more. Together, they’ve helped WebFX’s clients earn more than $3 billion in revenue from the web — and that’s just in the past five years. @webfx
Over the past several years, cyberattacks have made the news more and more in the United States.
There are a couple of reasons for that, but the fact of the matter is that US companies and government entities are frequently the targets of malicious cyberattacks, resulting in hacked websites, stolen user data, and astronomical financial losses.
But are cyberattacks really a threat to the average American business or individual? We researched the stats to find out, and the truth is frightening. 
How much cyberattacks cost the US
One of the most important parts about this infographic is how Keith B.
Alexander — the former head NSA, CSS, and USCC — calls cyberattacks “the greatest transfer of wealth in history.” His experience speaks for itself, which is a big part of the reason cyberattacks and hackers are so terrifying for US businesses. Is there anyone in the world who would know hackers better than a US general who ran three federal cyberwarfare departments? With his opinion in mind, let’s take a look at the facts that influenced him.
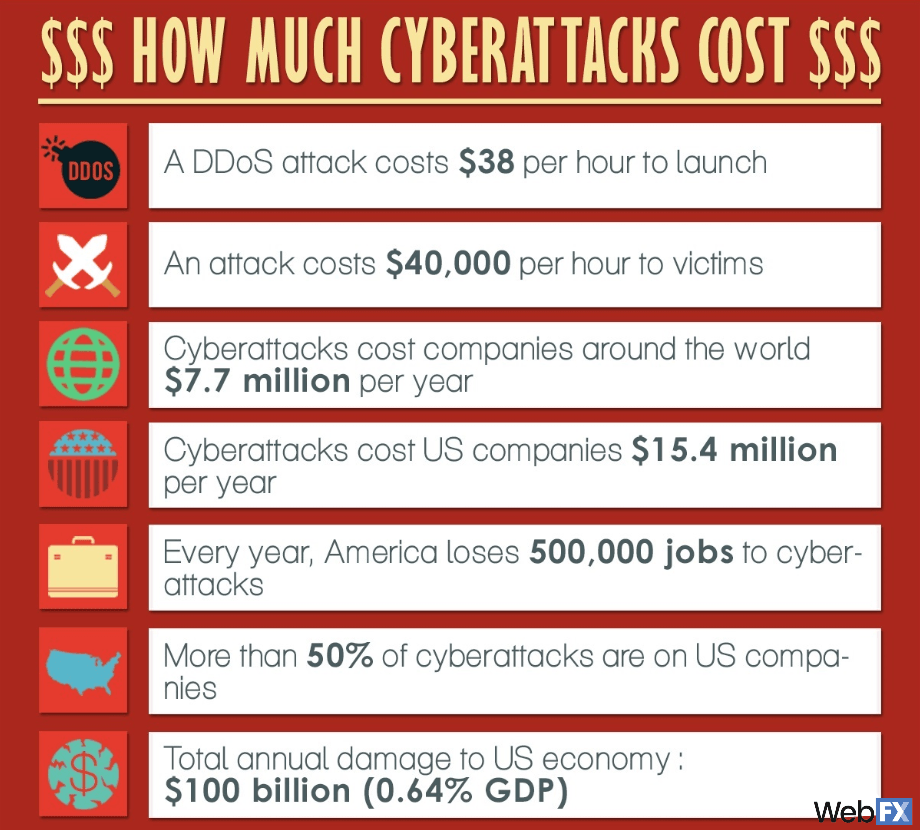 First, a distributed denial of service (DDoS) attack only costs $38 per hour to launch. So if someone wanted to take your site down for an entire workday — or even your peak hours — they could do it for less than $400. Granted, that’s a lot of money depending on who you ask. But at the same time, most people can probably afford to front $400 for a one-time fee. Especially when you consider how much damage they can do.
First, a distributed denial of service (DDoS) attack only costs $38 per hour to launch. So if someone wanted to take your site down for an entire workday — or even your peak hours — they could do it for less than $400. Granted, that’s a lot of money depending on who you ask. But at the same time, most people can probably afford to front $400 for a one-time fee. Especially when you consider how much damage they can do.
For every hour that they take your business’s company offline, they cost you $40,000 per hour in damages. For the hacker who’s only paying $38 per hour, they net $1052.63 in damages for every dollar they spend. That’s an incredible ROI in the worst way possible, and all it takes is an angry person with the right connections.
With that in mind, it’s no wonder cyberattacks cost companies around the world $7.7 million every year. And since half of the world’s cybercriminals target US entities, it’s no wonder that they cost US companies $15.4 million per year. As a direct result, the United States loses 500,000 jobs every year because of the money either stolen or prevented by cybercriminals.
Every year, the country loses $100 billion (or 0.64% of our GDP) purely to cybercrime.
The targets of cyberattacks
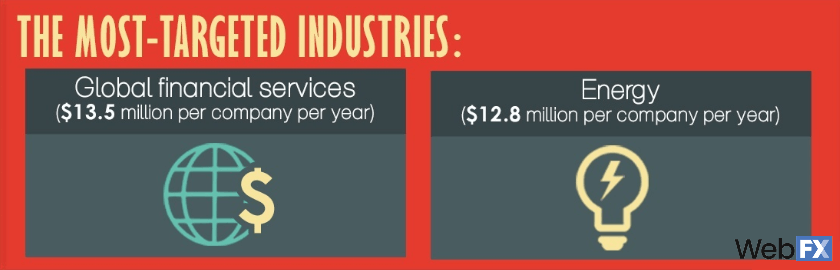 There are two industries that get hit the most by cyberattacks.
There are two industries that get hit the most by cyberattacks.
- Financial services
- Energy companies
Financial services are often hit because — obviously — they have money. Everything from stolen bank information to a hacked ATM is considered a cyberattack, and the hackers all directly benefit financially. There’s no middleman, no buyer, and no “hot” merchandise.
As long as they cover their tracks, they’re fine. But why are energy companies #2? You can’t profit directly from shutting down a power distributor’s grid, and you don’t make money if you destroy the infrastructure of an oil conglomerate.
In 2014, the US energy industry suffered 79 hacking incidents (that we know of). It’s nice to see that they’ve decreased since 2013, which had 145, but that also means hackers could be getting more sophisticated with their methods. After all, anti-hacking measures can only prevent hackers using today’s strategies.
If a hacker creates an innovative new way to enter your system, you couldn’t stop it since your prevention software isn’t ready for it. That means hackers are, unfortunately, always a step ahead. Plus, in June of 2015, Trend Micro’s chief cybersecurity officer said “the energy sector is woefully unprepared for protecting itself against cyberattacks.” Combine that with the fact that hackers are constantly figuring out new ways to attack companies via the Internet, and the energy industry makes an easy target for new hackers testing their skills or experienced hackers trying new attacks.
Regardless of their motivations or skill levels, the fact remains the same — energy companies are tempting targets for hackers.
The most popular kinds of cyberattacks
On the Internet, you have a lot of resources at your disposal. Information is available at the drop of a hat, and you can reach out to anyone with email, instant messaging, message boards, and other media.
That’s part of what makes it so easy — and affordable — for hackers to attack companies online.
DDoS
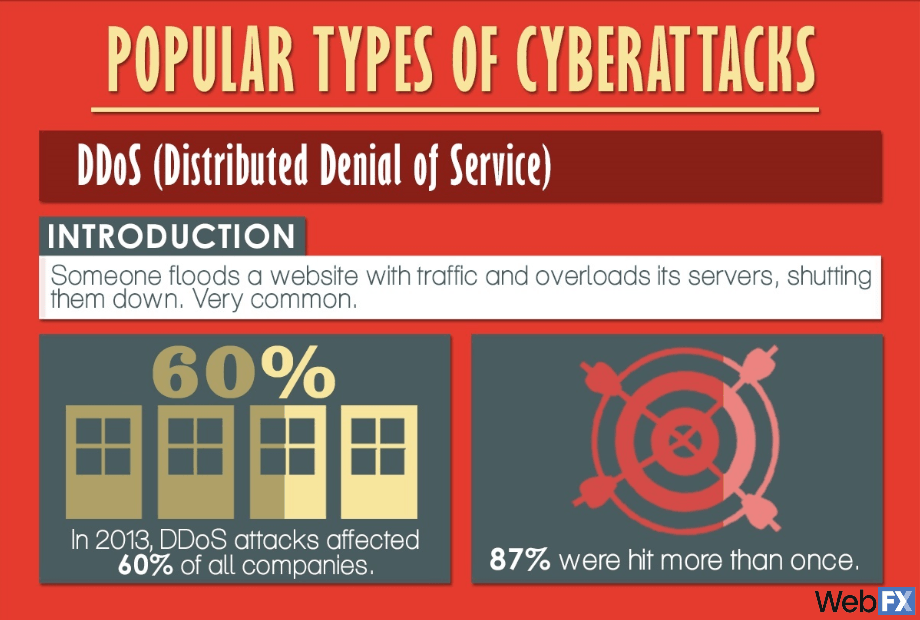 DDoS attacks are one of the most common types of cyberattacks in the world. In 2013, they affected 60% of all companies, and 87% of those companies were hit more than once.
DDoS attacks are one of the most common types of cyberattacks in the world. In 2013, they affected 60% of all companies, and 87% of those companies were hit more than once.
DDoS is used so frequently because it’s so easy. Someone just needs to write a script for bots (or organize lots of like-minded people) to flood the servers of a target. Once the servers are flooded, they go down, and the business can’t operate until the servers come back up.
But bandwidth isn’t infinite. If there’s constantly a huge number of visitors trying to access your site, you won’t be able to get back up and running. It’s just too much for your servers to process.
Ransomware
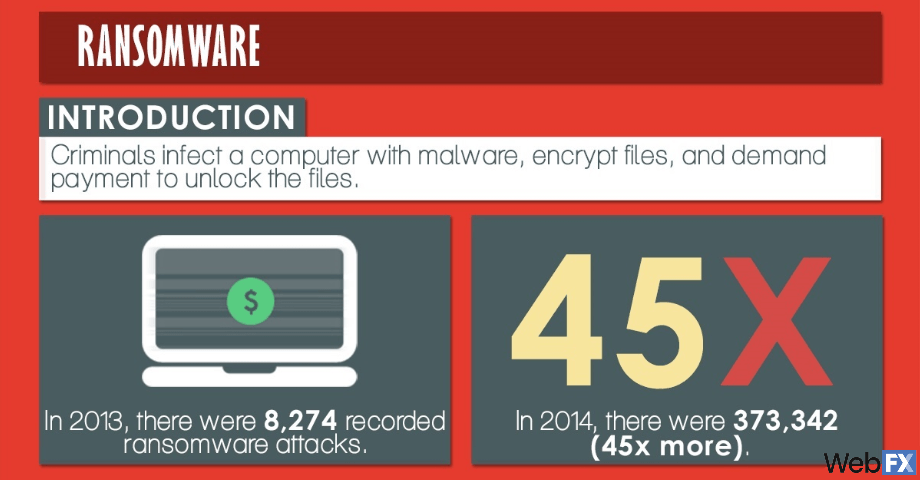 Ransomware is a sophisticated form of cyberattacks, and it has the potential to harm individuals just as much as companies. The idea is that a computer is somehow infected with malware that encrypts valuable files and demands a payment from you to unencrypt them. These files could be anything from family vacation photos to your customers’ credit card numbers.
Ransomware is a sophisticated form of cyberattacks, and it has the potential to harm individuals just as much as companies. The idea is that a computer is somehow infected with malware that encrypts valuable files and demands a payment from you to unencrypt them. These files could be anything from family vacation photos to your customers’ credit card numbers.
Either way, you’re in a bad situation. Unless you know an incredibly skilled cryptologist, your hands are probably tied. The most concerning part about ransomware is that it’s on the rise.
In 2013, there were 8274 recorded attacks. In 2014, there were 373,342 — 45 times more than the previous year. It could only take one ransomware attack to drain your bank account.
The best way to prevent it is to practice good habits online. But even that doesn’t always work. Hackers are getting smarter every day, and that means they’re getting more deceptive.
Spear phishing
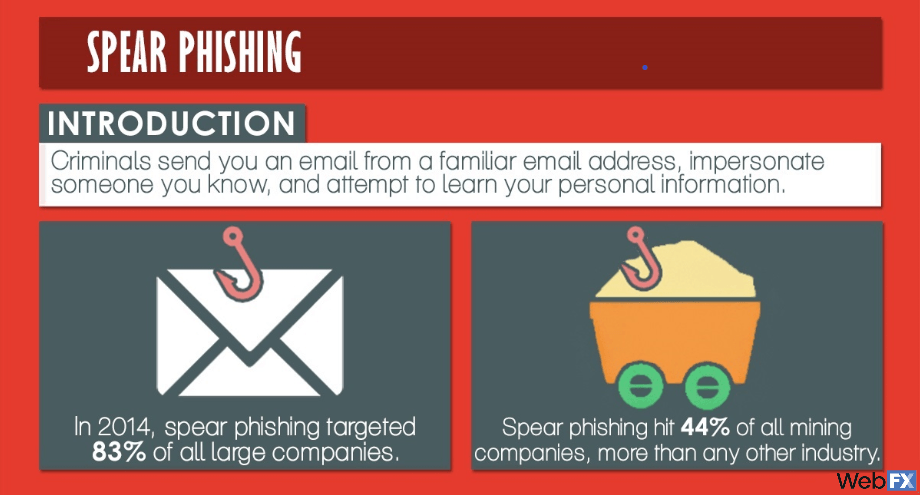 Phishing is the practice of sending people emails with attachments or links that infect your computer and steal your personal information. Spear phishing is a hyper-targeted, steroided version of phishing that looks at your emails, copies addresses you’ve used, and then sends you messages from those email addresses. So if your marketing team regularly hears from the president of your company, a spear phisher would see that, learn your president’s email address, and send you a message from that address.
Phishing is the practice of sending people emails with attachments or links that infect your computer and steal your personal information. Spear phishing is a hyper-targeted, steroided version of phishing that looks at your emails, copies addresses you’ve used, and then sends you messages from those email addresses. So if your marketing team regularly hears from the president of your company, a spear phisher would see that, learn your president’s email address, and send you a message from that address.
Then, they’d plant a link or an attachment in the email that you’d open, and without realizing it, you’d infect your computer (and company network) with malware. That malware could open a back door for a hacker to access your sensitive information, shut down your company’s internal communications, or attack your company in any number of other ways. While this hacking style might sound like it’s out of a movie script, it really works.
In 2014, 83% of all large companies in the world were targeted by spear phishing. And for some reason, they targeted 44% of all mining companies — more than any other industry in the world. That means approximately one in 2.7 mining companies were targeted by spear phishing.
For reference, your office building has a one in 161 chance of catching fire throughout the year. Even so, the financial industry deals with lots of cyberattacks throughout the year. The difference is that there are more financial institutions in the world than there are mining companies, so the risk for mining companies is higher since there are so few of them.
The most expensive cyberattacks
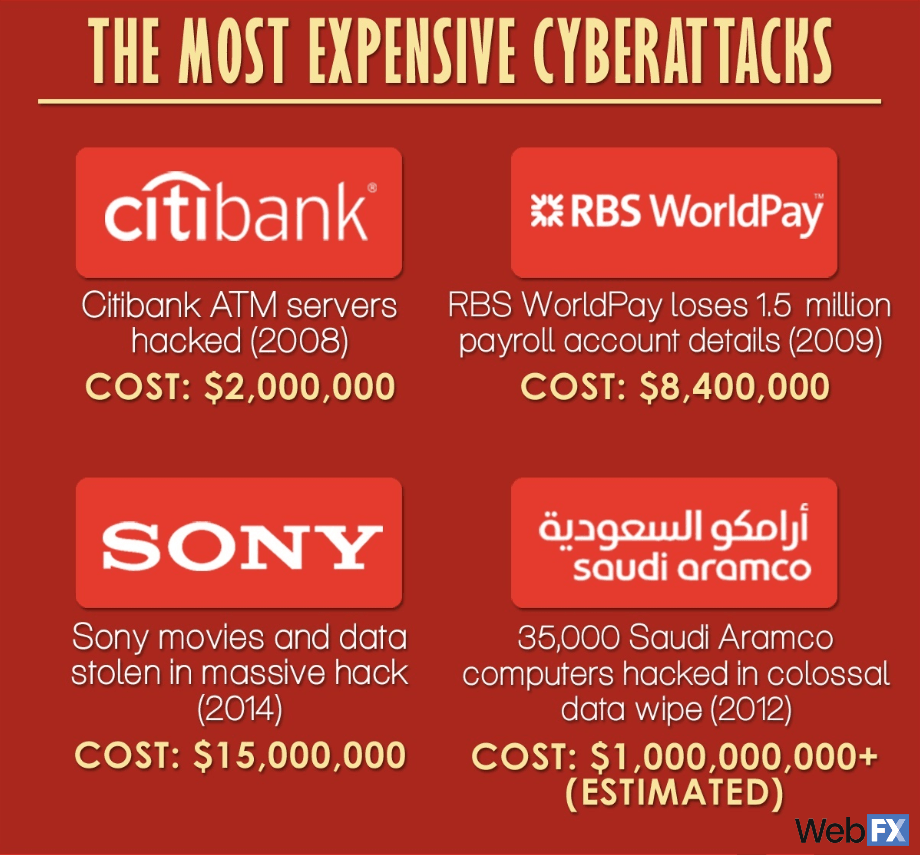 In 2008, a hacker targeted Citibank’s ATM servers and swiped about $2 million from the finance giant. That’s a lot of money, but it’s chump change when you look at other historical cyberattacks. There was also an attack in 2009 where RBS WorldPay lost 1.5 million payroll account details, which lost about $8.4 million for the company.
In 2008, a hacker targeted Citibank’s ATM servers and swiped about $2 million from the finance giant. That’s a lot of money, but it’s chump change when you look at other historical cyberattacks. There was also an attack in 2009 where RBS WorldPay lost 1.5 million payroll account details, which lost about $8.4 million for the company.
In one of the most famous cyberattacks of all time, Sony’s database of movies and other information was hacked in 2014, costing the company about $15 million in damages. And, to top it all off, Saudi Aramco was hacked during Ramadan in 2012, essentially setting the company back to 1970s technology. So, for weeks after the attack, one of the world’s most valuable companies had to do business by faxes, typewriters, and hands.
That huge data loss and corporate slow-down amounted to an estimated $1 billion in damages, which hasn’t been confirmed or denied by Saudi Aramco. Since the company is privately owned by the Al Saud royal family, they don’t have to publish those details.
Hackers and small businesses
 But not every hacking victim is a megalithic, multi-national corporation.
But not every hacking victim is a megalithic, multi-national corporation.
In fact, a lot of them are classified as small businesses, or companies with fewer than 500 employees. But hackers target companies even smaller than that, with 71% of cyberattacks targeting businesses that employ fewer than 100 people. In addition, 95% of all Visa credit card breaches relate to small businesses, and 44% of all small businesses suffered a cyberattack in 2014. Hackers could target small businesses for any number of reasons, but it’s probable that their small size and budgets makes them prime targets. These small businesses have working finances and personal information of customers, whether those are individual credit card numbers or the sensitive details of another business. Plus, small businesses probably don’t have the same world-class security as big corporations.
They’re smaller and they earn less — so they have less. While the average cost of a cyberattack on a small business hovers around $8700, that’s still a lot of money when you have a small staff. And depending on how your business is doing, that could be all it takes to shut you down for good.
How to protect yourself and your business from cyberattacks
While hackers are always innovating and trying out new attacks, there are some standard “rules” that you can keep in mind to keep yourself and your business safe from cyberattacks.
Before an attack
 Check your finances weekly. That includes your bank account, credit cards, 401k, and anything else you do with your money. Never open attachments in emails from unknown senders. Even if the message sounds harmless, that attachment is a different story.
Check your finances weekly. That includes your bank account, credit cards, 401k, and anything else you do with your money. Never open attachments in emails from unknown senders. Even if the message sounds harmless, that attachment is a different story.
Enter URLs by hand instead of clicking links. Like attachments, links can look safe as they install malware on your computers. Don’t click any links an email sends you — instead, hover over the link to see the full address. If you feel comfortable with it, enter it by hand.
Never save passwords on your phone or computer. If you have to save them somewhere, write them down by hand and keep them in a locked drawer of your desk. If you don’t have a locked drawer, keep them somewhere else that’s safe. Regularly change passwords. The average lifetime of a good password is six months.
Set calendar reminders for yourself to update all of your passwords at least twice per year. Never text or IM personal information. Even if you have an encrypted messaging service, you never know who could intercept or decode your messages. Only buy from or submit information to websites with HTTPS security. HTTPS shows you that a company or person has taken essential steps to securing their website.
While HTTPS doesn’t guarantee against a hack, it does act as a deterrent and a solid line of defense. Use SSL or HTTPS for your business’s website. Since you’re only going to submit information to HTTPS secured websites, it’s only smart for you to use it too. It’ll show your visitors that you’re dedicated to protecting their valuable information.
Regularly scan your site and computers for malware. While some hackers try to stay one step ahead of other companies, most of them will use methods that have been around for years. That means regularly scanning your site and computers for malware will let you catch the majority of cyberattacks and malicious software before it has a chance to do any damage. Regularly assess your site for vulnerabilities. On top of malware, you also need to check your site’s code, security protocols, and other prevention measures on a regular basis.
Set up an anti-virus or anti-malware program to automatically check your throughout the week. Store digital keys and certificates in a secure, tamper-proof, cryptographic data storage container. If you use any kind of digital keys or certifications to access your site, keep them stored somewhere secure. If you don’t trust any kind of encryption with some of your information, you can always store it in an offline container — just make sure you create and track backups.
During and after an attack
 If worse comes to worst and you’re hit by a cyberattack, it’s critical that you react quickly and intelligently. These steps will help you get rid of any malware, worms, or viruses that have infected your systems beyond repair.
If worse comes to worst and you’re hit by a cyberattack, it’s critical that you react quickly and intelligently. These steps will help you get rid of any malware, worms, or viruses that have infected your systems beyond repair.
- Disconnect your device(s) from the Internet
- Perform a full system restore
- Re-install all protection software
- Update all protection software
- Call all necessary entities to ensure your information is secure
After you’ve done all of that, you can concentrate on how the cyberattack hit you or your business and what you can do to prevent another one in the future.
Cyberattacks and you
No matter where you work, what you do, or how you behave online, cyberattacks are a real threat. One of the best things you can do is share this information with others who need it!
Use our social buttons and let us know what you think on Twitter!
-
 The WebFX team is made up of more than 450 subject matter experts in digital marketing, SEO, web design and web development, social media, and more. Together, they’ve helped WebFX’s clients earn more than $3 billion in revenue from the web — and that’s just in the past five years.@webfx
The WebFX team is made up of more than 450 subject matter experts in digital marketing, SEO, web design and web development, social media, and more. Together, they’ve helped WebFX’s clients earn more than $3 billion in revenue from the web — and that’s just in the past five years.@webfx -

WebFX is a full-service marketing agency with 1,100+ client reviews and a 4.9-star rating on Clutch! Find out how our expert team and revenue-accelerating tech can drive results for you! Learn more
The Internet in Real Time
Ever wonder how much is going on at once on the Internet? It can be tough to wrap your mind around it, but we’ve put together a nice visual that’ll help! The numbers show no sign of slowing down either.
Find out More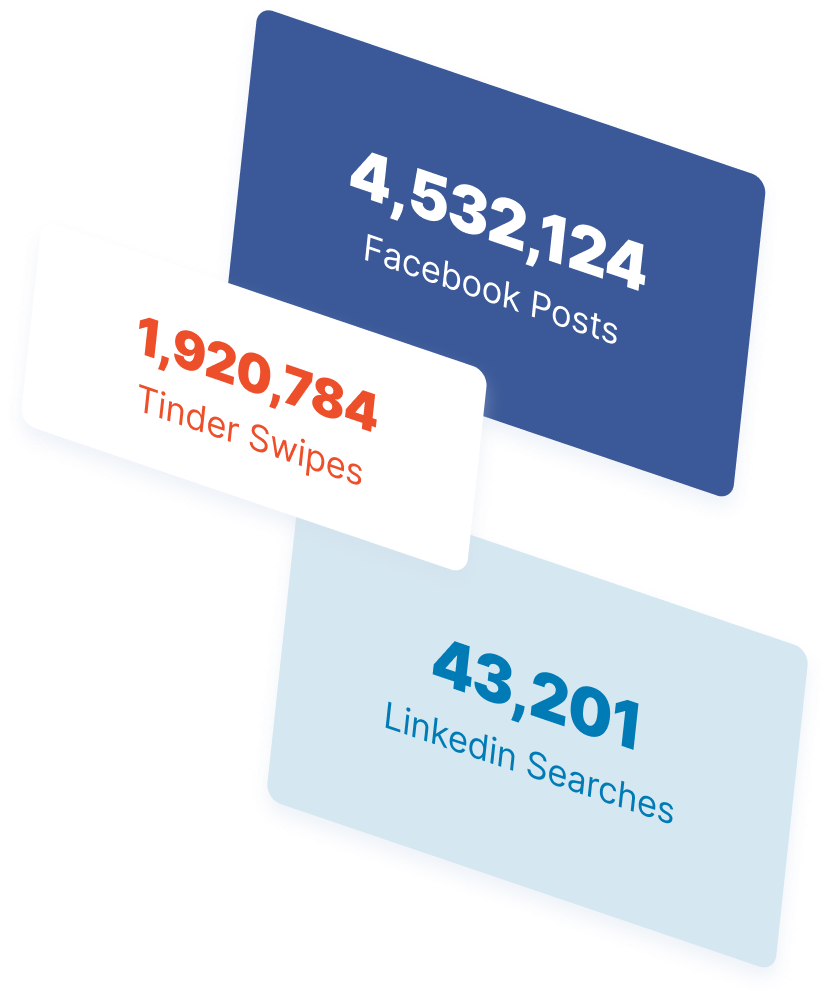

Ready to Drive Results for Your Business?
See how WebFX uses SEO, PPC, Social Media, and Web Design to Drive Revenue for Businesses.
Get InspiredThe Internet in Real Time
Ever wonder how much is going on at once on the Internet? It can be tough to wrap your mind around it, but we’ve put together a nice visual that’ll help! The numbers show no sign of slowing down either.
Find out More